SASE, or Secure Access Service Edge, is a technology framework that merges wide-area networking (WAN) and network security solutions into a cloud-based service. This model is designed to provide a simple, flexible, and agile infrastructure that ensures consistent user experiences, enhanced application performance, and reduced security risks, regardless of user location or the nature of applications and workloads.
Building on this foundation, Unified SASE as a Service integrates these networking and security services into a single, cohesive platform. It enhances network scalability, agility, and security by delivering these capabilities as a unified, tightly integrated service. Key features include a unified control plane, single-pass architecture, and flexible delivery options, allowing organizations to implement and manage the solution according to their specific needs and pace. This advanced approach simplifies the management of network and security functions, making it an ideal solution for organizations looking to streamline their IT infrastructure while enhancing overall performance and security.
| Category | Unified SASE as a Service | Managed SASE |
|---|---|---|
| Architecture | Employs a single-pass architecture that allows for comprehensive inspections and processing of data packets only once, ensuring consistent policy enforcement without impacting user performance. | May not necessarily use a single-pass architecture and could involve multiple processing steps, potentially affecting performance and policy consistency. |
| Integration | Offers tightly integrated network, security, and observability services, providing a seamless experience that reduces operational complexity. | Often involves multiple point solutions that are stitched together, leading to operational complexity and prolonged deployments. |
| Control and Flexibility | Provides flexible delivery options, allowing organizations to choose from self-managed, co-managed, and fully managed service delivery, enhancing control and customization. | Typically focuses on managed services, which may limit the level of control and customization available to the organization. |
| Global Network | Leverages a global private network backbone, ensuring high performance and reliability across geographies. | May rely on multiple service providers with inconsistent service level agreements (SLAs), potentially affecting performance and reliability. |
| User Experience | Aims to deliver a better user experience by reducing costs and complexity while ensuring performance, agility, and security. | May face challenges in providing a consistent user experience due to the integration of multiple vendor solutions, affecting overall service quality. |
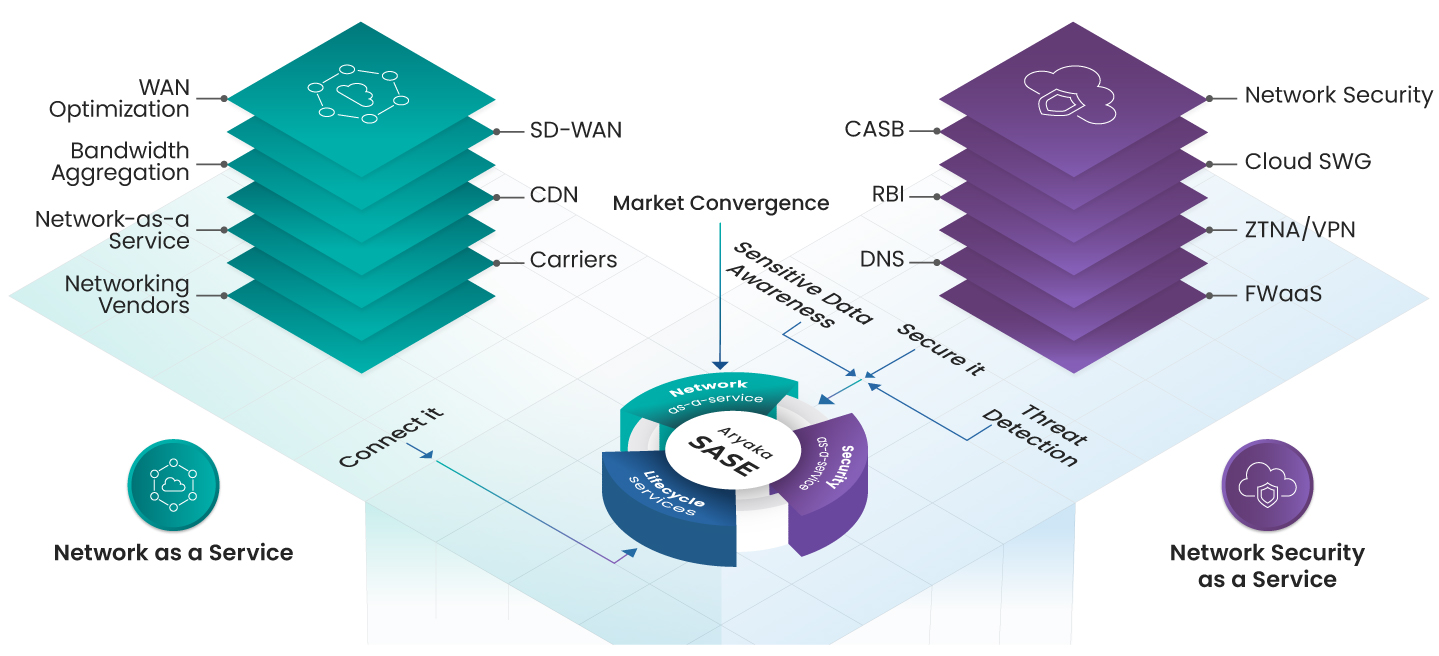
Unified SASE as a Service differs from traditional network security solutions in several key ways. Traditional solutions were often deployed on-premises and focused on keeping network and security within the organizational framework. In contrast, Unified SASE as a Service is cloud-based, making it more flexible and scalable to meet the changing needs of modern enterprises. It integrates multiple network and security technologies into a single cloud-based solution, combining security with networking functions and user experience. This unified approach reduces complexity, enhances performance, and provides a more seamless user experience compared to traditional, hardware-centric solutions. Additionally, Unified SASE as a Service supports a hybrid workforce by providing secure access to data and applications across distributed environments and helps in cost optimization by reducing the need for multiple point products and lowering both capital and operational expenditures.
The SASE framework has evolved significantly over the years, particularly during the early stages of the COVID-19 pandemic when organizations urgently needed to secure network access and corporate resources for a fully remote workforce. Initially, the integration of VPN and SD-WAN with cloud-based security services such as Firewall as a service, URL filtering, Anti-malware, cloud access security broker, and intrusion detection and prevention was common. This period saw the emergence of concepts like single-vendor SASE and multi-vendor SASE.
As the framework matured, SASE deployments began to incorporate more advanced security technologies including data loss prevention (DLP), enterprise browser isolation, and Zero Trust Network Access (ZTNA). The integration of advanced analytics and artificial intelligence (AI) also became standard to enhance the detection and response to security threats in real-time. However, these advancements introduced new complexities, such as the need to manage multiple point solutions and the lack of a unified policy management model, which in turn increased costs and deployment time.
Unified SASE as a Service addresses these challenges by offering a unified control plane that ensures consistent policy application across various security and network functions. It integrates traditionally siloed products like SD-WAN and Next-Gen Firewall into a single-pass architecture, simplifying the security landscape. Additionally, it provides flexible delivery options, including self-managed, co-managed, or Aryaka-managed service delivery, catering to different organizational needs.
Key features of Unified SASE as a Service also include a single pane of glass for management and provisioning, which simplifies the oversight and operation of network and security functions. This approach not only reduces the network attack surface but also improves SaaS and multi-cloud application performance, enhancing overall business and operational agility. These features make Unified SASE as a Service an optimal solution for modern enterprises looking to streamline their network and security infrastructure while adapting to the evolving digital landscape.