Unified SASE: The Solution to Frankenstein Networks

The evolution of WAN networks and network security has been rapid over the past 20 years. Prior to 2000, WAN networks were relatively straightforward, with private networks (such as MPLS and leased lines) combined with centralized firewalls placed at headquarters and data centers. At that time, most employees worked from the office and were tethered to a cable; there was no cloud to speak of. Remote workers were connected to a central VPN concentrator. While private networks provided a high-performance controlled experience, they were expensive. However, with the limited number of remote workers, subpar experience was not considered a significant issue. There were almost no firewalls in branch offices, and a centrally located firewall protected connections to the internet. The network and security teams were organized into separate silos and only occasionally collaborated with each other.
Over the past 25 years, a slew of new technologies has disrupted the established order, including Wi-Fi in 1997, broadband internet in 2000, WAN optimization in 2002, cloud services in 2006, cloud security in 2008, SD-WAN in 2012, and SASE (Secure Access Service Edge) in 2019. As a result, IT and security organizations have been grappling with three fundamental questions:
Question One: Where to place the breakout to the internet?
Before Wi-Fi became ubiquitous, it was common practice to route all internet traffic over the private WAN to a central location where a collection of firewalls would protect the perimeter of the enterprise. However, as Wi-Fi and cloud adoption became more widespread, backhauling massive amounts of internet traffic over expensive private links started to compromise application performance. Consequently, there has been a growing trend of placing the internet breakout in branch offices and deploying firewalls in these locations, despite the added cost and heightened security risk. Cloud security came to the rescue in 2008, providing an ideal solution for smaller offices and remote workers, allowing them to keep firewalls away from on-premises and eliminate hair-pinning for remote users. For large sites and data centers, the on-premises NextGen Firewall remained in place, creating the challenge that security policies were now split between cloud and on-premises security.
Question Two: How can cheaper internet be used to slash enterprise WAN costs?
Most corporations have refrained from connecting offices directly to the internet for simplicity, and security reasons. However, as Wi-Fi and cloud adoption forced the hands of IT managers and the internet was introduced to all offices, internet connectivity was increasingly seen as an opportunity to slash WAN expenses. This droves the adoption of SD-WAN, which used path steering and optimization capabilities to deliver the required application performance by using the optimal path (internet or MPLS) where required. The biggest benefit of SD-WAN was cost reduction by reducing the need for expensive (and inflexible) MPLS as much as possible by directing WAN traffic across internet circuits. Today, many companies have even eliminated MPLS altogether and replaced it with (dual) internet links. However, the internet is a best-effort technology with inconsistent latencies and without bandwidth guarantees. This has created the emerging need for enhanced internet with an uptime guarantee and more predictable latencies. Additionally, with the explosion of apps on the WAN, network managers want to eliminate any cause of subpar application performance. Also, with the increase in work-from-anywhere, it became apparent that remote workers would need to enjoy the same experience as office workers. Traditional SD-WAN solutions primarily focused on office connectivity, which often resulted in increased network complexity and higher management overhead.
Question Three: What cloud-onramp architecture best adapts to ever-changing cloud needs?
With the widespread adoption of cloud services, companies are now dealing with the challenge of managing connections between their WAN and cloud providers. This requires specific cloud-onramps that aggregate connections from multiple offices and remote users onto a single link to a specific cloud provider’s IaaS location. Cloud-onramps are costly, as each on-ramp requires specific aggregation points within a specific location. Moreover, these cloud-onramps must fit into the overall security framework of the company, which often involves a combination of on-premises firewalls and cloud security covering both the internet breakout use case and site-to-site connections.
The End Result: IT Organizations Are Stuck with Frankenstein Networks.”
IT organizations have been struggling to come up with simple answers to the three aforementioned questions and are now facing a complex and challenging situation. They are left with a patchwork of separate implementations for SDWAN to connect branch offices, cloud-onramps, and security implementations for cloud and on-premises security. These different implementations often come from multiple vendors and with separate management tools, leading to a complex and cumbersome solution to manage and maintain. This “Frankenstein network” is complex and results in subpar performance, inconsistent security policies, and a lack of visibility and control, making it challenging to address issues quickly and efficiently.
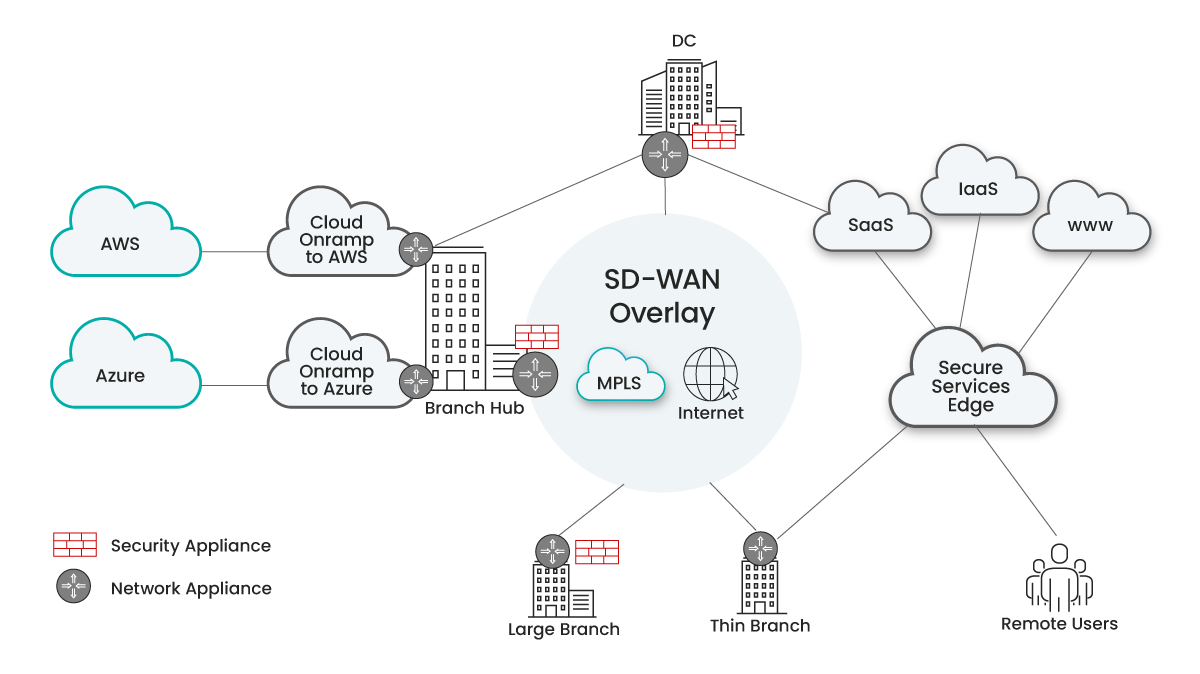
Today’s Typical Frankenstein Networks
“Aryaka’s SASE Solution: The End of Frankenstein Networks”
The rise of Frankenstein networks has left IT organizations searching for a solution, and SASE has emerged as the answer. Aryaka’s approach to SASE begins with a high-performance network foundation, allowing for secure connections between users and applications regardless of location, all under a set of fully unified policies for networking and security. By enforcing security policies as close to users and applications as possible, whether in the cloud or on-premises, performance bottlenecks are eliminated in compliance with zero-trust principles. The network foundation must eliminate the inflexible patchwork of separate networks connecting branch offices, users, data centers, and the cloud and be delivered as a consumable cloud service, including on-premises functionality. Moreover, a flexible network infrastructure must offer three service levels to optimize WAN expenses: best-effort internet, better-than-internet, and better-than-MPLS, while completely eliminating legacy MPLS. It’s often worth noting that current single-vendor SASE implementations appear to be SASE solutions at the surface level, but underneath the hood, they can still be Frankenstein networks that have not cleaned up the underlying architecture.
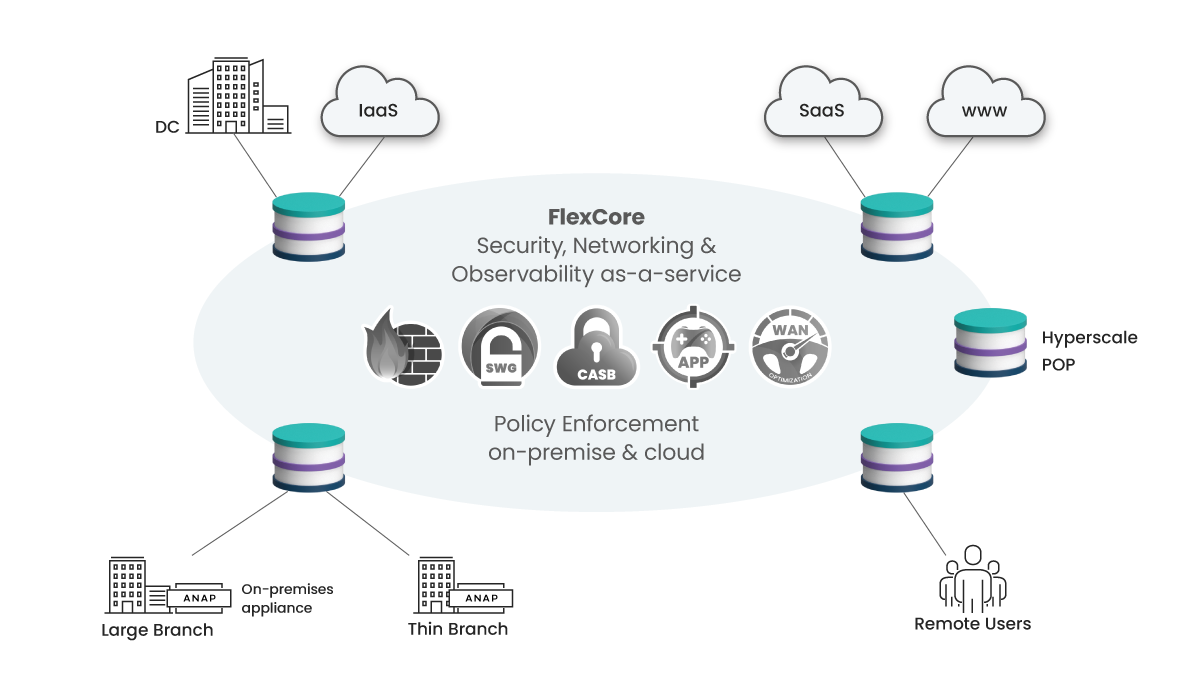
Aryaka’s Unified SASE ona FlexCore Foundation
The outcomes of Aryaka’s approach provide an easy-to-consume SASE solution that benefits customers by delivering a highly secure and high-performance experience for all users, applications, and workloads. This easy consumption is established by a cloud-native infrastructure consisting of deterministic control of the network underlay, combined with a single-path architecture of networking, optimization, and security functions with integrated service workflows. Agility and flexibility are the fundamental upshots for customers, as they can now evolve their networking and security infrastructure in pace with the never-ending digital transformation. Moreover, with this approach, users can quickly move, and branch offices can be relocated without constantly replacing technologies and vendors every few years as new challenges arise. Additionally, expensive cloud-onramps can be eliminated without requiring costly upgrades to the network infrastructure. Network SLAs (Service Level Agreements), ranging from best effort to guaranteed application performance, can be changed instantly based on users’ needs and the nature of applications. Aryaka’s SASE solution, with its easy consumption, agility, flexibility, and managed services, provides customers with a powerful tool to eliminate Frankenstein networks and take control of their network and security infrastructure.










