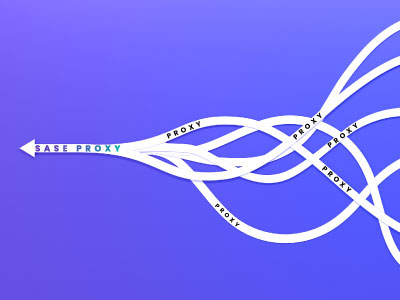
Maximizing the SASE Performance: The Vital Role of ‘At Scale’ Distributed Enforcement
Network security deployment architectures undergo regular evolution, driven by various enterprise requirements. Some of the Industry recent trends are outlined below: Minimizing the cost & maintenance burden associated with disparate and multiple network security systems. Implementing a[...]
Read Post >