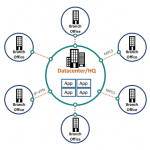
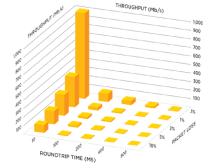
Make Security Simple: Streamline Policies in Unified SASEBalancing Configuration and Control is critical for reducing security risks and management complexity
The Secure Access Service Edge (SASE) service, along with its associated architecture, comprises a powerful amalgamation of multiple security components. These include a stateful inspection firewall, Intrusion Detection and Prevention System (IDPS), DNS security, DoS/DDoS protection, Secure Web Gateway (SWG), Zero Trust Network Architecture (ZTNA), Cloud Access Security Broker (CASB), and many more. These components […]